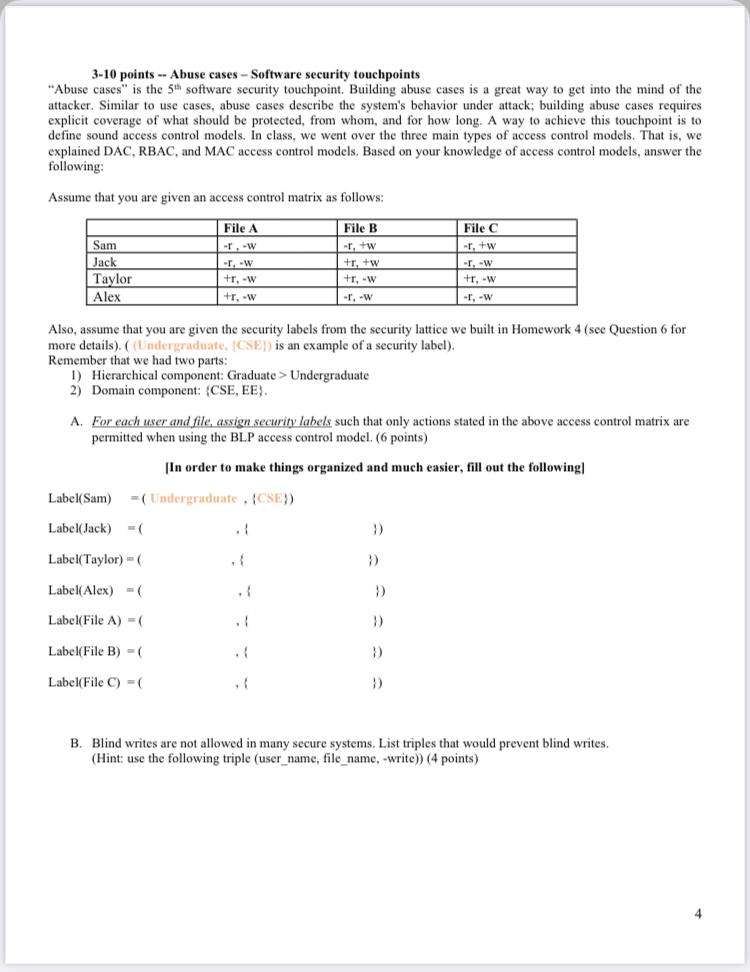
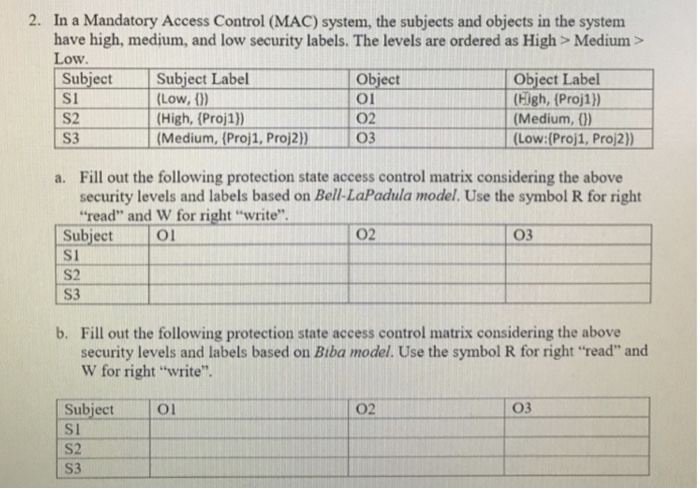
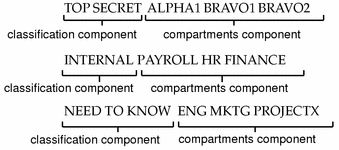
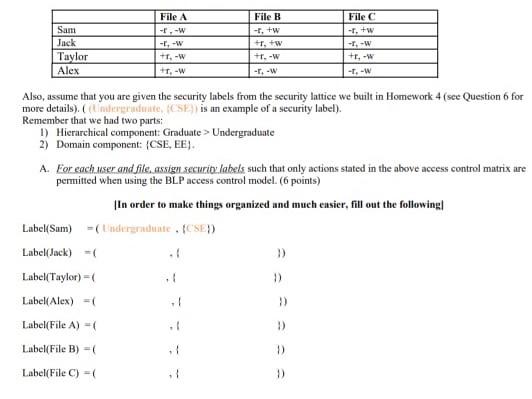
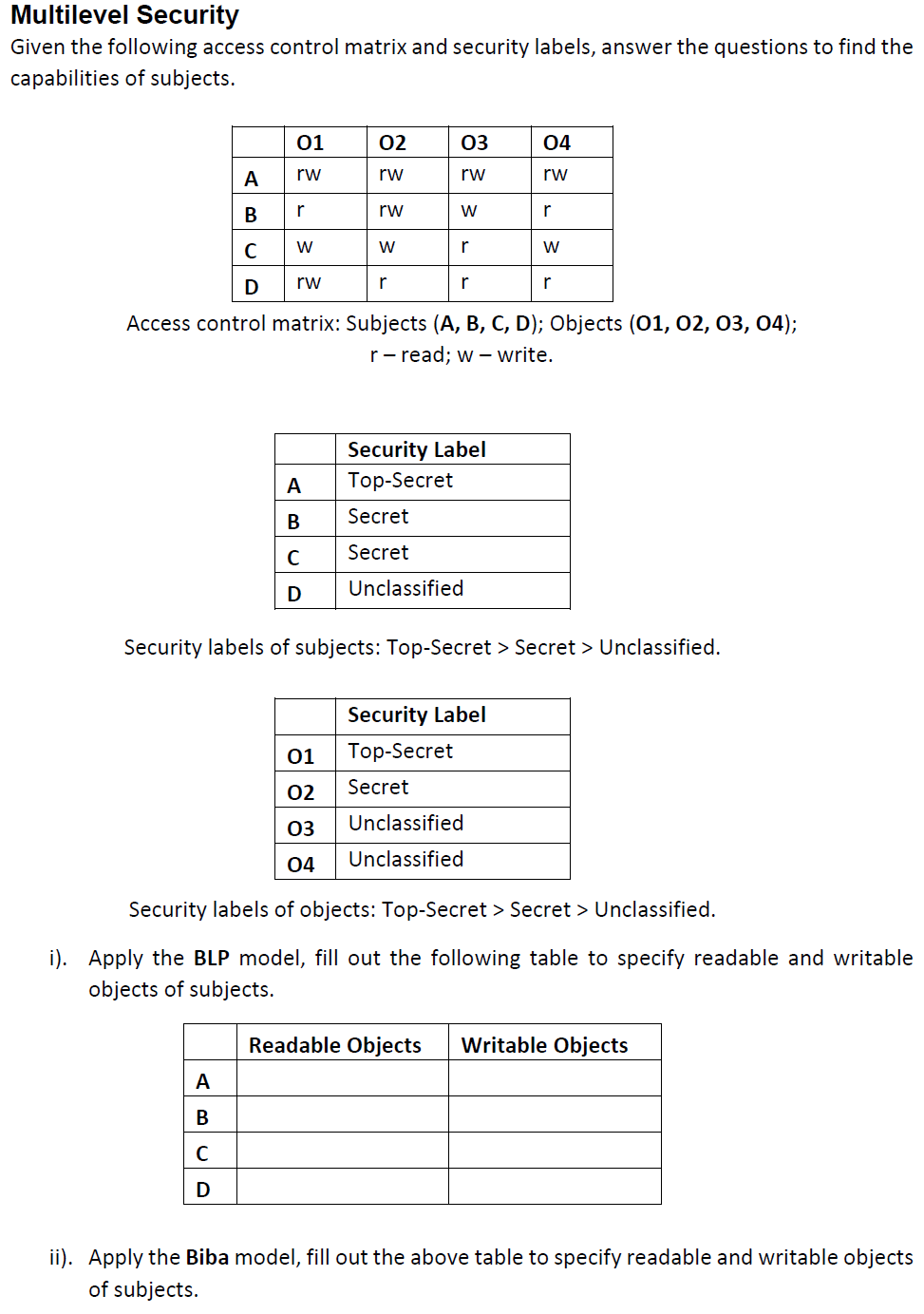
45 security labels access control
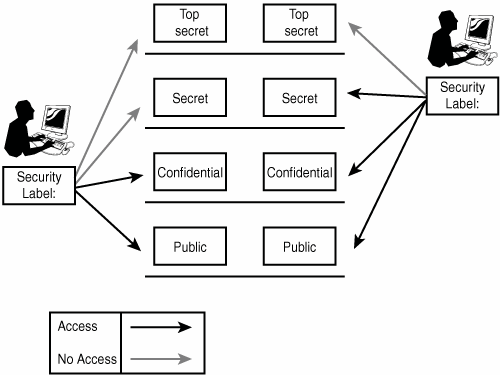
cloud.google.com › column-level-security-introIntroduction to column-level access control | BigQuery ... Oct 01, 2022 · Using BigQuery column-level access control, you can create policies that check, at query time, whether a user has proper access. For example, a policy can enforce access checks such as: You must be in group:high-access to see the columns containing TYPE_SSN. To enhance column-level access control, you can optionally use dynamic data masking ... Access Control Models - UHWO Cyber Security - University of Hawai'i ... MAC uses "security labels" to assign resource objects on a system. There are two pieces of information connected to these security labels: classification (high, medium, low) and category (specific department or project - provides "need to know"). Each user account is also assigned classification and category properties.
Security: Access Control - Bosch Security and Safety Systems I Global Getting a connection error when accessing the AEC webpage When trying to access the Access Easy Controller via Microsoft Edge, Chrome or other web browsers, you may get an error, "the connection for this site is not secure", which prevents you from connecting to the AEC. No ratings 439 0 03-30-2022 Can I downgrade my AEC firmware to 2.1.8.5?

Security labels access control
Sensitivity labels for Microsoft Teams - Microsoft Teams A team owner can change the sensitivity label and the privacy setting of the team at any time by going to the team, and then click Edit team. Control guest access to teams. You can use sensitivity labels to control guest access to your teams. Teams created with a label that doesn't allow guest access are only available to users in your organization. Access control - Wikipedia In the fields of physical security and information security, access control ( AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization . 3 Understanding Access Controls and Privileges - Oracle 3 Understanding Access Controls and Privileges. Chapter 2 introduced the concept of labels (with their levels, compartments, and groups) and the basic notion of access control based on the row's data label and the user's label. The present chapter examines the access controls and privileges that determine the type of access users can have to labeled rows.
Security labels access control. Oracle Label Security Oracle Label Security uses row level data classifications to enforce access controls restricting users to only the data they are allowed to access. It enables organizations to control their operational and storage costs by enabling data with different levels of sensitivity to co-mingle within the same database. Oracle Label Security also provides a cost-efficient way to address regulatory requirements for managing access to data on a need to know basis. Control external access to resources in Azure Active Directory with ... Sensitivity labels help you control access to your content in Office 365 applications, and in containers like Microsoft Teams, Microsoft 365 Groups, and SharePoint sites. They can protect your content without hindering your users' collaboration and production abilities. Access control: Models and methods in the CISSP exam [updated 2022] Risk-Based Access Control is a dynamic access control model that determines access based on the level of evaluated risk involved in the transaction. One commonly-used example is identifying the risk profile of the user logging in. If the device being logged in from is not recognized, that could elevate the risk to prompt additional authentication. Secure external collaboration using sensitivity labels When you create a sensitivity label, you can either determine which users get which permissions to content that has the label applied, or you can allow your users make this decision when they apply the label (also commonly known as user-defined permissions or UDPs). Figure 1: Creating a new sensitivity label in the Microsoft 365 Compliance center.
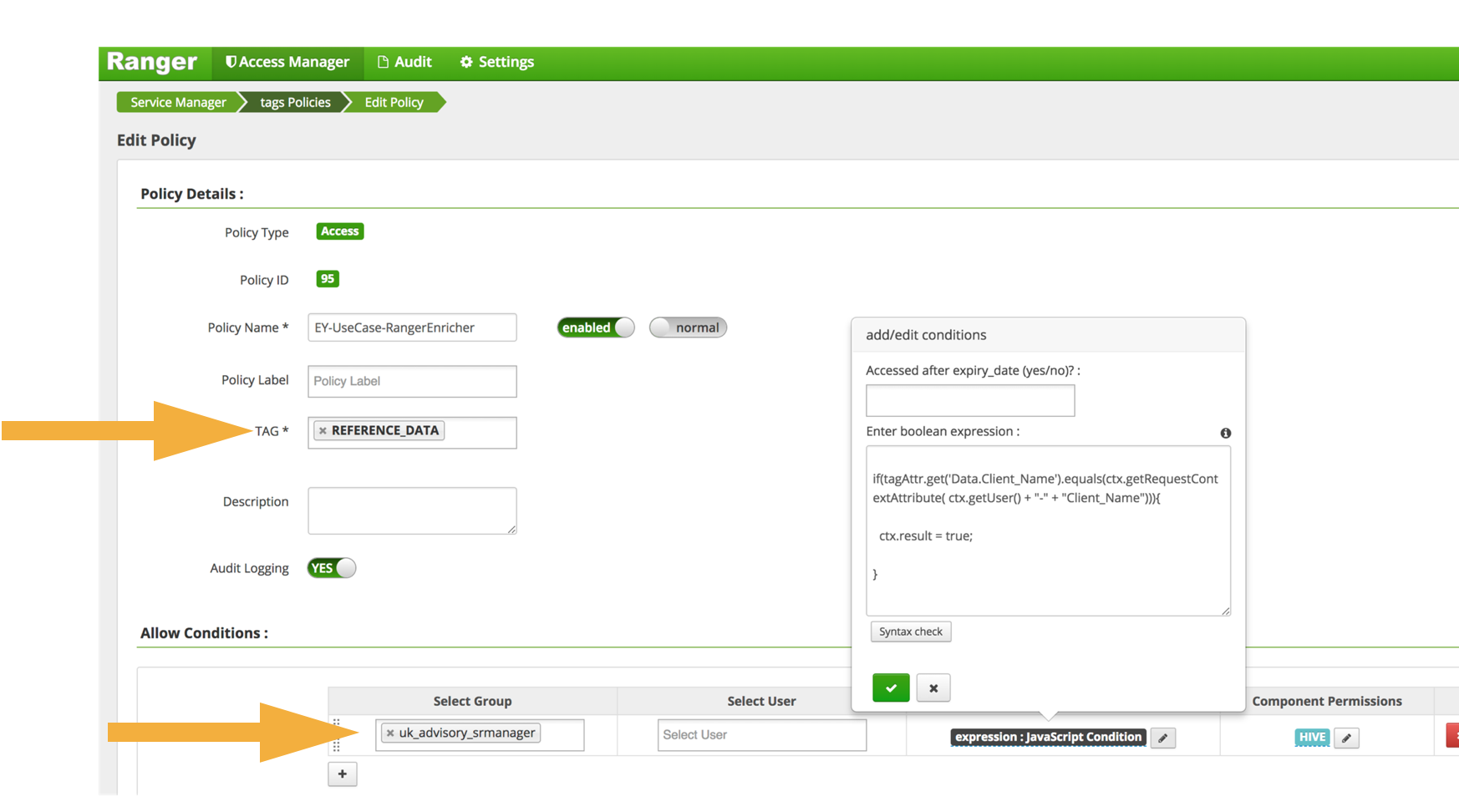
› digitalguide › serverMandatory Access Control: How does it work? - IONOS Oct 14, 2020 · There are a number of options available for implementing and maintaining access control, including Mandatory Access Control. This model is also used in the political and military branches, which require tamper-proof protection of data. Keep reading to find out how this rule-based access control works and what its pros and cons are. SECURITY LABEL - postgres-xc.sourceforge.net In practice, this facility is intended to allow integration with label-based mandatory access control (MAC) systems such as SE-Linux. Such systems make all access control decisions based on object labels, rather than traditional discretionary access control (DAC) concepts such as users and groups. Parameters object_name table_name.column_name learn.microsoft.com › en-us › office365Microsoft 365 guidance for security & compliance - Service ... Sep 19, 2022 · To benefit from the Conditional Access App Control capabilities in Defender for Cloud Apps, users must also be licensed for Azure Active Directory P1, which is included in Enterprise Mobility + Security F1/F3/E3/A3/G3, Enterprise Mobility + Security E5, Microsoft 365 E3/A3/G3, Microsoft 365 E5/A5/G5, and Microsoft 365 E5/A5/G5/F5 Security and ... How security labels control access - ibm.com Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES). You construct these labels with security label components, which represent different levels of data classification and access authority.
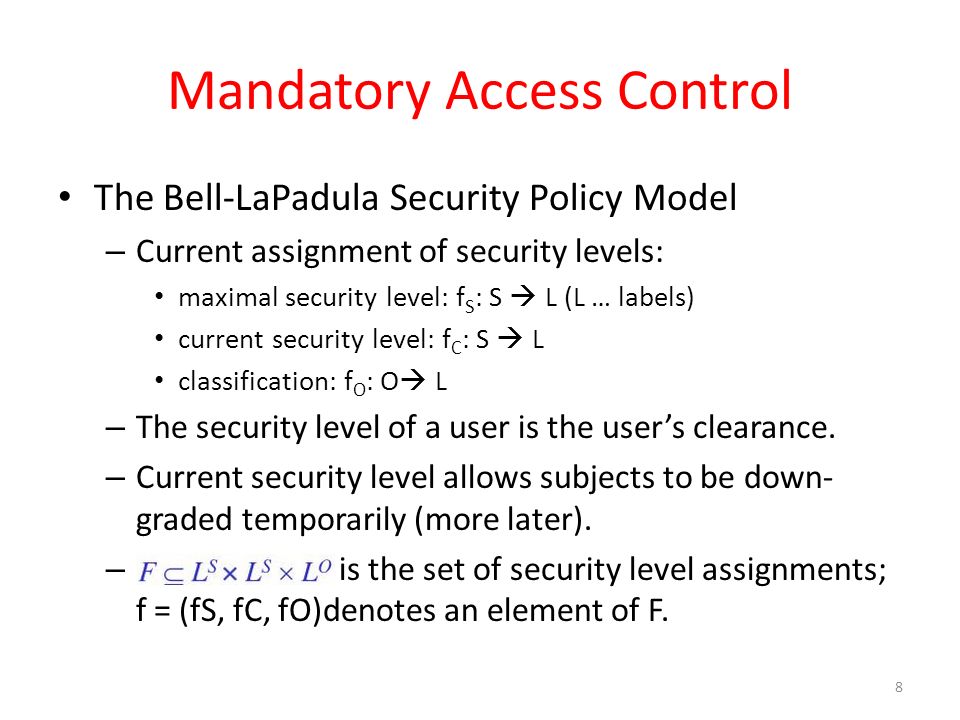
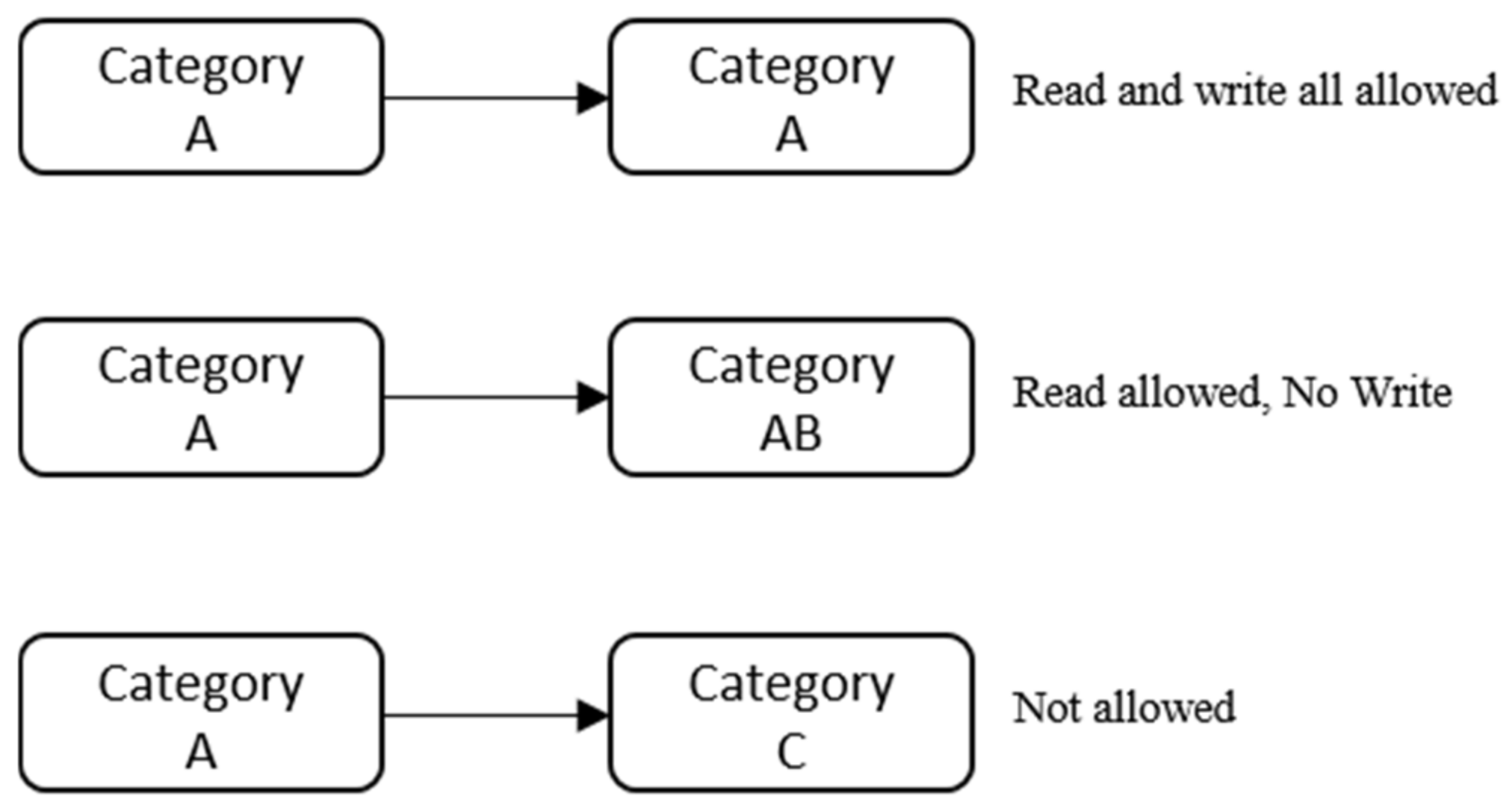
Lattice-based access control - Wikipedia In this type of label-based mandatory access control model, a lattice is used to define the levels of security that an object may have and that a subject may have access to. The subject is only allowed to access an object if the security level of the subject is greater than or equal to that of the object. Label Security | Oracle Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance. Learn more about Oracle Database security. Watch the overview video (8:16) Mandatory access control - Wikipedia In computer security, mandatory access control refers to a type of access control by which the operating system or database constrains the ability of a subject or initiator to access or generally perform some sort of operation on an object or target. In the case of operating systems, a subject is usually a process or thread; objects are constructs such as files, directories, TCP/UDP ports, shared memory segments, IO devices, etc. Subjects and objects each have a set of security attributes. Whene Access Control: Understanding Windows File And Registry Permissions ... This integrity label is used to establish the "low" label that marks the Internet Explorer process used in LowRights Internet Explorer. "System" and "high" labels are used to protect critical system resources. The Windows message pump filters messages based upon the integrity level of the message.
Access Control using Security Labels & Security Clearance - Isode Security Labels provide an important mechanism for controlling access to information in many high security environments, and are also useful in environments with lower security requirements. This paper provides a reasonably detailed description of how security labels and clearances work, while attempting to avoid the high level of technical complexity seen in many papers in this area.
What Are the Different Types of Access Control? - JumpCloud Organizations can — and often do — use different types of access control in different environments. Subjects are the entities that do the accessing — like users and applications. Objects are the entities that receive access — like networks and files. DAC: Discretionary access control. MAC: Mandatory access control.
Security-labels - FHIR v4.3.0 - Health Level Seven International A security label is a concept attached to a resource or bundle that provides specific security metadata about the information it is fixed to. The Access Control decision engine uses the security label together with any provenance resources associated with the resource and other metadata (e.g. the resource type, resource contents, etc.) to
› fhir › securitySecurity - FHIR v4.3.0 - Health Level Seven International Authorization/Access Control - FHIR defines a Security Label infrastructure to support access control management. FHIR may also define a set of resources to administer access control management, but does not define any at present ... Access control constraints may result in data returned in a read or search being redacted or otherwise ...
Access Control Types and Models - Identity Management Institute® Access control list or ACL is a file, typically referred to a computer file system, which attaches permissions to an object or entity. An ACL specifies which users or system processes are granted access to objects, as well as what operations the objects are allowed. Each entry in a typical ACL specifies a subject and an operation.
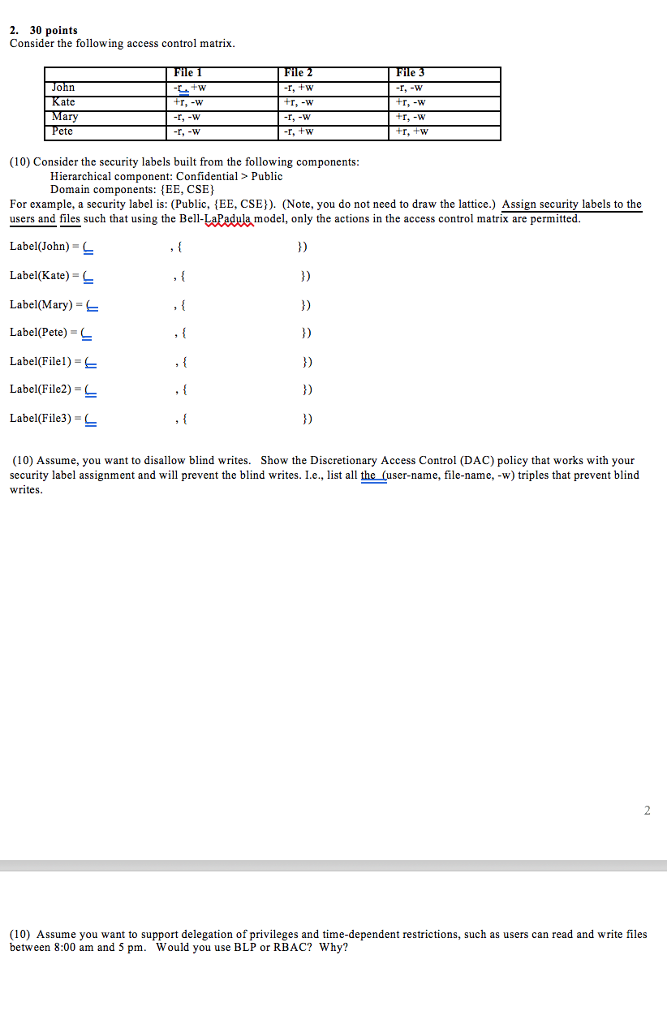
Define access control list and capability list and compare them ... The Discretionary Security Property: use of an access matrix to specify the discretionary access control. SE Linux, like most other systems that protect multi-level data, uses the BLP model. This model specifies how information can flow within the system based on labels attached to each subject and object.
Oracle Label Security vs Fine Grained Access Control Oracle Label Security vs Fine Grained Access Control Tom,I recently read an article on Oracle Label Security and from the relatively limited information provided in the article, Label Security seem very similar to Fine Grained Access Control, maybe just a bit more limited than FGAC.Why do both these technologies exist and how would one choose
cloud.google.com › docs › access-control-foldersAccess control for folders with IAM | Resource Manager ... Sep 28, 2022 · IAM lets you adopt the security principle of least privilege, so you grant only the necessary access to your resources. IAM lets you control who (users) has what access (roles) to which resources by setting IAM policies. IAM policies grant specific role(s) to a user giving the user certain permissions.
Mandatory Access Control - CGISecurity Mandatory Access Control (MAC) ensures that the enforcement of organizational security policy does not rely on voluntary web application user compliance. MAC secures information by assigning sensitivity labels on information and comparing this to the level of sensitivity a user is operating at. In general, MAC access control
› TR › sparql11-querySPARQL 1.1 Query Language - W3 1 Introduction. RDF is a directed, labeled graph data format for representing information in the Web. RDF is often used to represent, among other things, personal information, social networks, metadata about digital artifacts, as well as to provide a means of integration over disparate sources of information.
Security label components Security label components are security objects for defining security policies. The elements of these components are used to define security labels, which control access to protected tables. Security label components represent any criteria that your organization might use to decide if a user must have access to a table row or column.
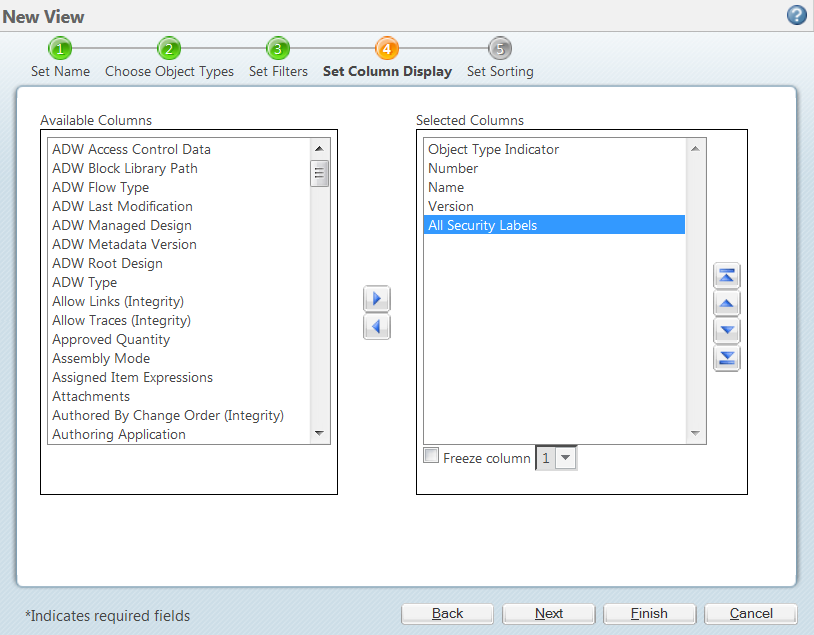
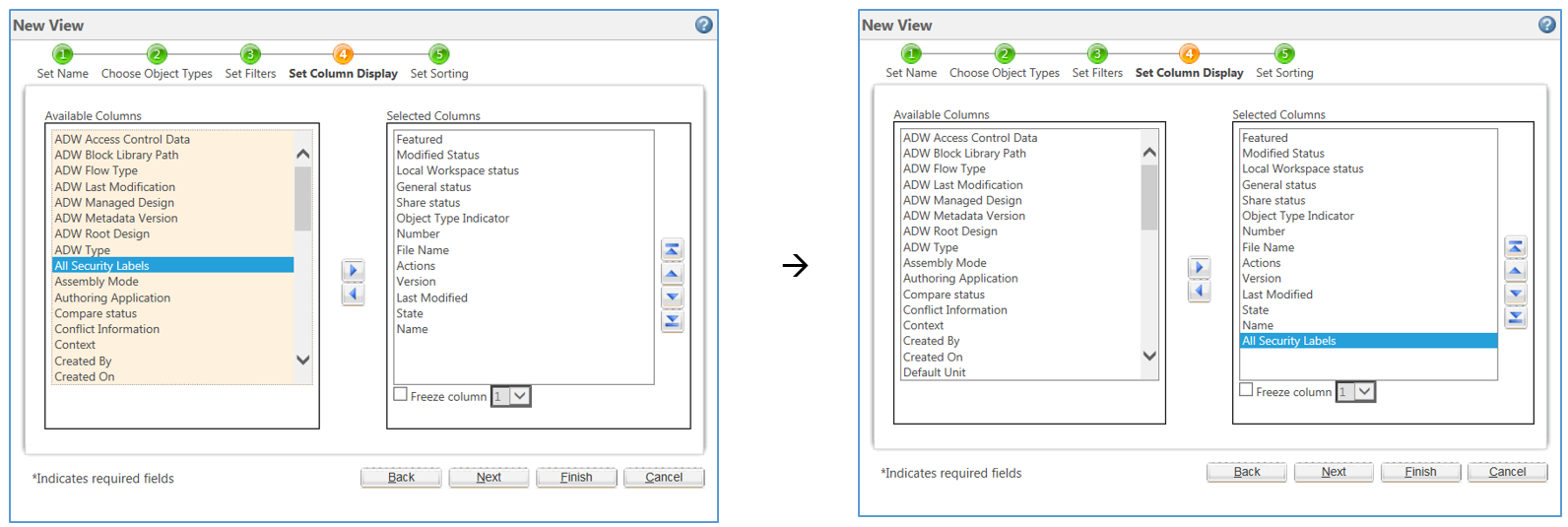
Security Labels and Access Control - support.ptc.com To access an object, a user must be cleared for all security labels, either as an authorized participant or by an active agreement, and have proper access control permissions for that object. The following flow chart provides an overview of how Windchill processes security labels and access control to grant or deny a user access to an object.
Label-based access control (LBAC) overview - IBM LBAC security labels. In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to data in order to protect the data. They are granted to users to allow them to access protected data. Format for security label values.
techcommunity.microsoft.com › t5 › microsoftMulti-tenant access for Managed Security Service Providers Jul 20, 2020 · Turning on role-based access control will cause users with read-only permissions (for example, users assigned to Azure AD Security reader role) to lose access until they are assigned to a role. Users with admin permissions are automatically assigned the default built-in Microsoft Defender ATP global administrator role with full permissions.
Using Security Labels for Directory Access and Replication Control - Isode Security Label based access control will still provide value, but the granularity of ...
Use of Security labels & access controls for nationally ... - PTC Use of Security labels & access controls for nationally classified information. I have a requirement to restrict access to the meta data and content (documents) in Windchill based on a security context. Not only do I need to restrict access, but I need to store the content in a specific location, which will be in a different location to the ...
3 Understanding Access Controls and Privileges - Oracle 3 Understanding Access Controls and Privileges. Chapter 2 introduced the concept of labels (with their levels, compartments, and groups) and the basic notion of access control based on the row's data label and the user's label. The present chapter examines the access controls and privileges that determine the type of access users can have to labeled rows.
Access control - Wikipedia In the fields of physical security and information security, access control ( AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization .
Sensitivity labels for Microsoft Teams - Microsoft Teams A team owner can change the sensitivity label and the privacy setting of the team at any time by going to the team, and then click Edit team. Control guest access to teams. You can use sensitivity labels to control guest access to your teams. Teams created with a label that doesn't allow guest access are only available to users in your organization.



!['Mandatory Access Control Essentials with SELinux': Costas Senekkis, ICSI [CRESTCon 2019]](https://i.ytimg.com/vi/h4eG8y53D9Q/maxresdefault.jpg)











![PDF] A System for Supporting The Cyber Security Control of ...](https://d3i71xaburhd42.cloudfront.net/e24f299c73998f565a63fa1258a15c55ab10c816/2-Table1-1.png)







Post a Comment for "45 security labels access control"